Guarded Key
is the most secure multi-platform password manager.
(Watch on
youtube)
Top Features
-
One-Click Sign In - sign into your favorite web sites with one-click
-
One Password - use one password forever and forget passwords for your online accounts
-
Cryptographic Security Token - dynamic security token based on Certificate/RSA Signature
-
Portable License - manage your online identities on USB flash drive on any computer/platform
-
Financial Information - manage all your bank account information and credit/debit cards
-
Contacts (address book) - names, birth dates, addresses, phone numbers, emails, social networks
-
Products - manage software licenses, product codes, activation keys, online resources
-
Strong Encryption - protect your accounts with 4096-bit key and 8 layers of encryption
-
Touch Screen - use touch screen and finger gestures to browse online accounts
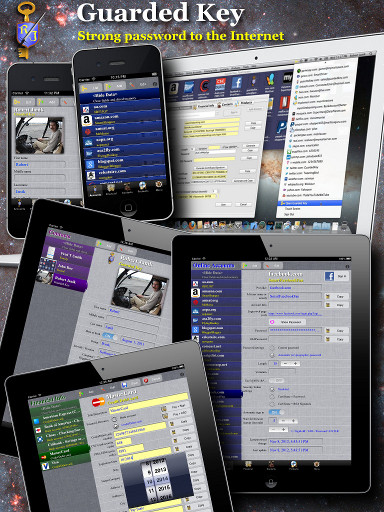
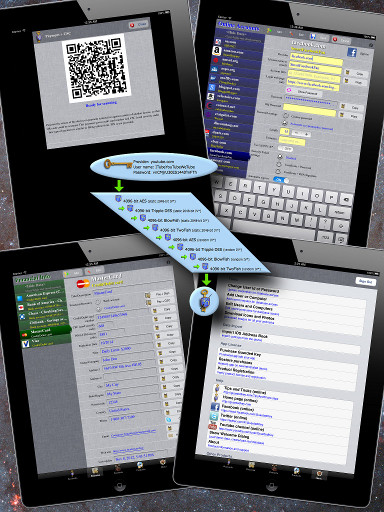
Download Guarded Key and try full version for free for upto 60 days.
How does it work?
Guarded Key is the most secure password manager
which uses encrypted database to store all your online identities, bank accounts, credit/debit cards,
contact information, product codes (software activation keys, serial numbers, registration codes).
Each record in the database is encrypted with 4096-bit key and 8 layers of encryption
consisting of different encryption standards (AES, Triple DES, Blowfish, Twofish).
Encrypted database can only be accessed after providing valid credentials defined by username and password (this is the only password you have to remember).
Database is protected so well, that breaking 10 character password would take on a personal computer 8 billion years.
Touch screen and task bar icon with popup menu provides easy navigation in the list of online accounts.
Password generator can help you to create strong password for each account.
Touch screen tap or one click in popup menu decrypts information about selected account and performs automatic sign in.
It starts web browser, navigates to login url and enters username and password. When done, data in memory is shredded (overwritten with zeros) so that it is not exposed to potential viruses or spyware.
The application keeps decrypted information in memory only as long as necessary and the data is shredded as soon as possible. When you select a database record for viewing or editing,
it is decrypted and after selecting another record or minimizing the application, the data is shredded again. This keeps all your online identities and other information safe but ready for use.
The application uses per database licensing (not per computer). This allows you to use your Guarded Key on any computer (and even any OS platform) without installing the application or
paying for additional licenses. Just plug-in your USB flash drive or memory card and launch Guarded Key.
Forget all your passwords and get Guarded Key, your strong password to the Internet!
Other Features
-
Browser independence - use with any web browser of your choice
-
Universal license - use one license on unlimited number of computers and on all OS platforms
-
Auto-generated password - let Guarded Key generate strong password for each account
-
Custom password - choose password, if you don't want to use auto-generated password
-
Optional info - your other data is encrypted (membership Id, PIN, expiration date etc.)
-
Computer management - enhance safety by authorizing computers for Guarded Key sign-in
-
User management - add users with their own passwords for access to shared online accounts
-
Copy & paste installation - copy executable file and your encrypted database where you need it
Account Management
Guarded Key allows you to add all your online accounts into the encrypted database, generate password or enter custom password and
add optional information you would like to keep. This allows you to maintain email accounts, social network identities, online store accounts,
credentials for access to file sharing services for your multimedia content etc. You are allowed to setup as many accounts and as many user Ids per each
internet provider as you need.
Sign into your favourite web sites with one-click
Setup your online accounts for one-click automatic sign in (supports millions of web sites from around the world).
The application needs to specify web address for sign in (Url), how many seconds to wait for browser to start and load the page,
sign in sequence, which defines what buttons need to be pressed in order to navigate on the page and enter username and password.
Use one password forever
Is it hard to remember password for each and every of your online accounts? Then
forget it!
Guarded Key allows using one password to access all your online identities in an
encrypted database. Each of your online accounts can use different password which
you can change at any time, but you do not have to remember it. Your Guarded Key password will remain in
effect forever (unless you decide to change it too)
and it is safe even if you lose your portable key with encrypted database (USB flash drive or memory card).
One password forever? How strong is it? Is it safe?
Password for access to the Guarded Key database must be well chosen in order to make it secure in case you lose your portable USB flash drive or
somebody steals your computer. It is a good practice to use alphanumeric characters, have some letters capitalized and use punctuation marks (characters!@#$%^&*() etc).
Don't use words in any part of your password (like FastCar300) as this can easily be broken by dictionary attack. These recommendations are valid generally.
How long should my password be to make it safe? When determining password length we usually look at how long it would take to decipher enrypted database using
brute force attack and trying all combinations of characters to determine what the password is.
This is sufficient as there is not known method (mathematical algorithm) to make decryption faster without knowing user id and password or encryption key.
Time needed to break into the database
|
Password length
|
Personal computer with Intel Core 2 Duo processor
|
Supercomputer system 100000x faster than personal computer
|
All personal computers in the world
(10 billion computers)
|
|
6 characters
|
137 years
|
12.0 hours
|
0.434 seconds
|
|
8 characters
|
1040752 years
(approx. 1 million years)
|
10.4 years
|
54.7 minutes
|
|
10 characters
|
7877454788 years
(approx. 8 billion years)
|
78775 years
|
288 days
(approx. 9.5 months)
|
|
12 characters
|
59624455289668 years
(approx. 59624 billion years)
|
596244553 years
(approx. 596 million years)
|
5962 years
|
Table is valid for 4096-bit key and 8 layers of encryption - Guarded Key application
For most users 8 character password provides adequate protection.
Password with 12 characters or more provides such security, that encrypted database
cannot be broken even by somebody with corporate/government resources and concentrated effort
involving supercomputers or large network of personal computers.
Cryptographic Security Token authentication
Using static password to sign into online accounts of high importance may not provide adequate protection. Using secure connection HTTPS does not guarantee
total protection either. Foreign governments are now investing into supercomputers and sometimes manage to redirect internet trafic through their networks.
We can only speculate what they do with the data. Network communication can be saved for later analysis and even HTTPS can be broken when given time and resources,
therefore static passwords used for authentication may become compromised. Another type of attack can be data leaks through security holes or
leaks from inside the company providing online service (administrators/programmers stealing data).
How can we better protect our bank accounts, brokerage accounts, retirement funds and
even online shopping accounts?
The best protection can provide only dynamic authentication, where sign-in information changes for every online session.
Guarded Key password manager introduces Cryptographic Security Token as the most secure form of authentication.
How does it work?
Security token is an encrypted text which contains authentication information and timestamp. New security token is generated every second and a unique token is used for each sign in.
Each security token is valid for a short period of time (for example +/- 10 seconds) to resolve possible time difference between client computer and server.
Web server accepts only a security token with timestamp within this predefined range.
If timestamp falls outside of this time range, it is considered invalid. Security token can be used for authentication only once, after that it becomes invalid.
Guarded Key security token can be generated using one of two methods:
-
Certificate + Password
- timestamp and password is encrypted using 4096-bit key and 8 layers of encryption consisting of AES, 3DES, Blowfish, Twofish.
4096-bit key is used as "Certificate" which encrypts and validates communication between client and online provider.
Client sends security token which is decrypted on server side, and password and timestamp is evaluated.
Password is not stored on the server, but hash is used instead.
-
Certificate + RSA Signature
- timestamp is signed by RSA signature (RSA private key known only to user) and then this information is encrypted using
4096-bit key and 8 layers of encryption consisting of AES, 3DES, Blowfish, Twofish.
The key is used as "Certificate" which encrypts and validates communication between client and online provider.
Client sends security token which is decrypted on server side, and timestamp and RSA signature is evaluated by RSA public key.
Only owner of RSA signature (private key) is able to create valid security token.
This process completely eliminates use of Password (although password can be used for initial exchange of certificate and RSA keys and then disabled).
Your account is protected from data leaks on the side of the online provider, account is protected from use of old security tokens found by hackers by deciphering network communication,
use of spyware on your computer, key loggers and other types of computer attacks.
Note: If you successfully sign in and then need to sign in from another computer, you may need to wait at least 1 second (or more if computer time is not well synchronized),
before attempting another sign in, because Guarded Key generates a new security token with new timestamp every second.
Information about Security Token implementation can be found here.
Manage all your online identities on USB flash drive
Copy Guarded Key application with your encrypted database to a USB flash drive or memory card. You will create
a portable key which you can use to sign into your favourite web sites from any computer and any OS platform,
as well as access information about your bank accounts, retreive credit/debit card numbers,
obtain contact information, addresses, phone numbers, email addresses, social network links and
product codes, software activation keys and other information stored in the database.
Create as many backup USB keys as you need. You are getting one license for unlimited
number of computers. Guarded Key grants you per database license (not per computer license).
Your database with the application can be copied without limitations.
It is very easy to create your portable password manager
on USB flash drive or memory card. Just copy executable file for each platform and your encrypted database into the same folder on a portable storage,
or follow these steps.
Manage all your Bank account information and Credit/Debit cards
Guarded Key provides great tool to manage information about bank accounts and credit/debit cards in an encrypted database.
You can store Account number, Routing number, SWIFT code, IBAN, Credit/Debit card number,
CSC (card security code), which is useful for online shopping, PIN (ATM access code),
billing address or address of the financial institution (bank or credit card company),
Phone number, Email address and Website, so that you could quickly reach customer support.
Contacts (address book) - addresses, phone numbers, email, social networks
Add your contact information into an encrypted address book. You can define Name, Birth date,
home or work address, Cell/Home/Work Phone numbers, Personal/Work Email address, website, Social network links,
web address pointing to a photograph. You can download Photo to local storage (eg. USB drive) and
the photo will be displayed when contact is selected in the address book.
Manage Product codes, serial numbers, activation keys, social network links
Many hardware and software products require to keep Product codes, Serial numbers, Registration or Activation codes etc.
These are usually needed when software must be re-installed or when hardware manufacturer asks you to identify product in order to provide
customer service, allow download of software applications or drivers.
Guarded Key provides tool to maintain all this information in an encrypted database and much more.
You can maintain Product name, Version, name of the company, provider, manufacturer or distributor,
product registration information, Expiration date, Phone number, Email address, Website and Social network links.
Protect your data with 4096-bit encryption key and 8 layer encryption algorithm
No more worries about lost flash drives or paper diaries with plain text user names and passwords.
Guarded Key will protect your data with eight layers of encryption.
4096-bit key is used for each encryption layer. If one or more encryption methods
are found weak or even broken in the future, there is always another layer of protection
to give you certainty that a lost key has not become source of information for unauthorized
user and you have enough time to replace your lost key and change passwords if necessary.
For users with deeper interest in encryption method used, here is a simple scheme of the
algorithm:
 Provider: youtube.com
Provider: youtube.com
User name: ITubeYouTubeWeTube
Password: vnCMjrU30ES144JfmFTh
|

|
 4096-bit AES
(static 2048-bit IV*)
4096-bit AES
(static 2048-bit IV*)
|

 4096-bit Tripple DES
(static 2048-bit IV*)
4096-bit Tripple DES
(static 2048-bit IV*)
|

 4096-bit BlowFish
(static 2048-bit IV*)
4096-bit BlowFish
(static 2048-bit IV*)
|

 4096-bit TwoFish
(static 2048-bit IV*)
4096-bit TwoFish
(static 2048-bit IV*)
|

 4096-bit AES
(random IV*)
4096-bit AES
(random IV*)
|

 4096-bit Tripple DES
(random IV*)
4096-bit Tripple DES
(random IV*)
|

 4096-bit BlowFish
(random IV*)
4096-bit BlowFish
(random IV*)
|

 4096-bit TwoFish
(random IV*)
4096-bit TwoFish
(random IV*)
|

|

|
Encrypted Account (some characters cannot be displayed properly)
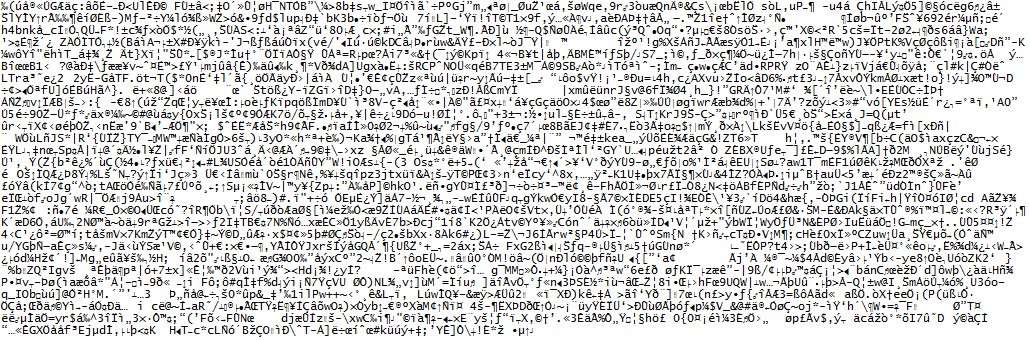
|
 Provider: youtube.com
Provider: youtube.com
User name: ITubeYouTubeWeTube
Password: vnCMjrU30ES144JfmFTh
|

|
 4096-bit AES
(static 2048-bit IV*)
4096-bit AES
(static 2048-bit IV*)
|

 4096-bit Tripple DES
(static 2048-bit IV*)
4096-bit Tripple DES
(static 2048-bit IV*)
|

 4096-bit BlowFish
(static 2048-bit IV*)
4096-bit BlowFish
(static 2048-bit IV*)
|

 4096-bit TwoFish
(static 2048-bit IV*)
4096-bit TwoFish
(static 2048-bit IV*)
|

 4096-bit AES
(random IV*)
4096-bit AES
(random IV*)
|

 4096-bit Tripple DES
(random IV*)
4096-bit Tripple DES
(random IV*)
|

 4096-bit BlowFish
(random IV*)
4096-bit BlowFish
(random IV*)
|

 4096-bit TwoFish
(random IV*)
4096-bit TwoFish
(random IV*)
|

|

|
Encrypted Account (some characters cannot be displayed properly)

|
* IV - Initialization Vector
Use touch screen and finger gestures to browse online accounts
Touch screen offers easy navigation through all your online identities and quick sign in. Browse accounts using finger gestures.
Swipe to the left and right to navigate through all thumbnails representing your accounts. Tap once or use mouse-click to start browser and sign in.
Well done. You have reviewed quite a lot of information.
What about trying Guarded Key? It's easy. Just click
Quick Start
Copyright (C) 2011-2016 Robert Janik, Brno, Czech Republic
|